Hi,
The latest stable Debian distributed for Rock5B by Radxa is this Bookworm image: https://github.com/radxa-build/rock-5b/releases/download/rsdk-b5/rock-5b_bookworm_kde_b5.output.img.xz
For clarity, doing “apt update; apt upgrade” is ALWAYS safe, right?
I would not want to take the risk that Debian had released a new kernel or u-boot version, and that version turns out to now have the RK3588 Rock5B specific patches, etc.
Inside https://docs.radxa.com/en/rock5/rock5b/radxa-os/using-apt I see a command under “Please run the following command to add the RadxaOS Vendor repository:”, it says “VENDOR… deb…”, and then “sudo apt-get dist-upgrade --allow-downgrades task-rockchip; sudo apt-get dist-upgrade --allow-downgrades”.
But, on the downloaded Debian image above these steps are already done so I don’t need to do them, right, or?
It would be a shame if a Rock5B suddenly is rendered unbootable and a whole system reinstall would be needed.
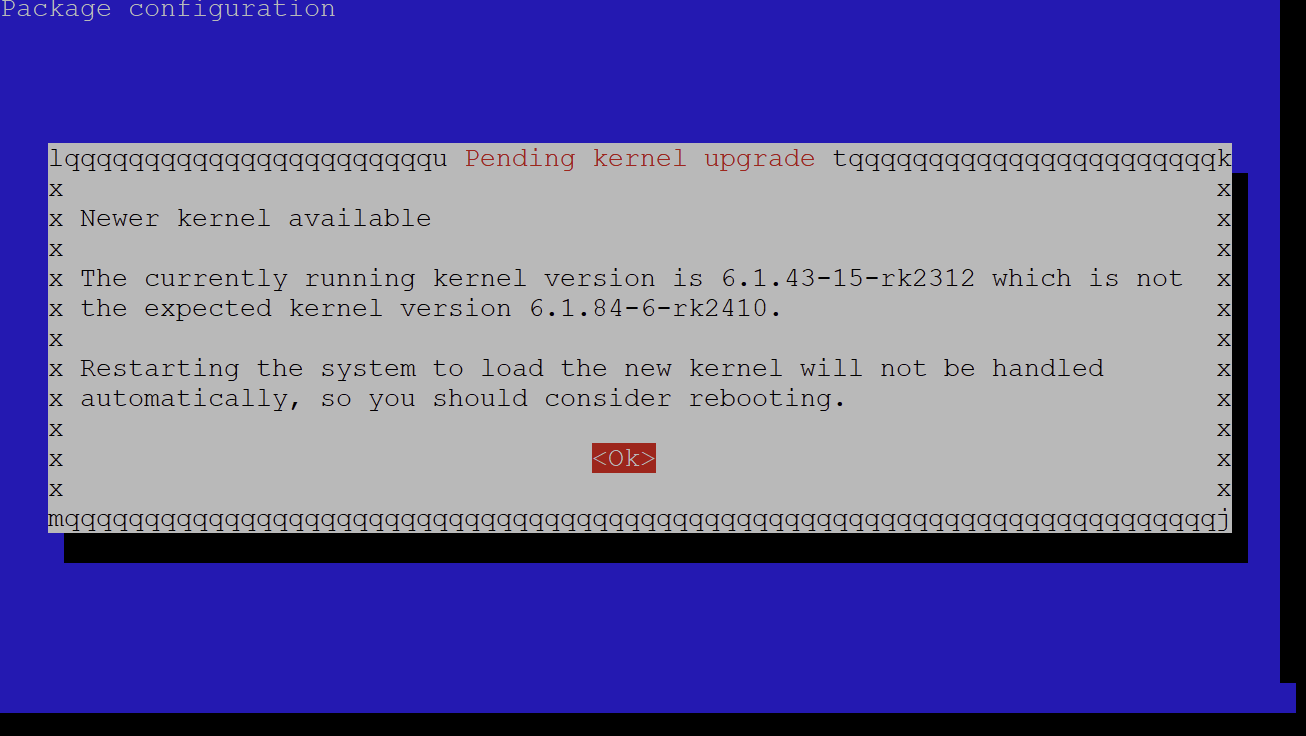
Right now I noticed apt upgrade shows this: “update-initramfs: Generating /boot/initrd.img-6.1.84-6-rk2410”, so kernel upgrades do happen.
The next line was “Couldn’t find EFI system partition. It is recommended to mount it to /boot or /efi.”.
It also said “Unpacking u-boot-rk2410 (2017.09-45-b9a0522) …”, not sure of what consequence that is.
Also interestingly “aptitude upgrade” started with this:
# aptitude upgrade
The following packages will be DOWNGRADED:
gstreamer1.0-plugins-good
The following NEW packages will be installed:
u-boot-rk2410{a}
The following packages will be REMOVED:
u-boot-rknext{u}
This is all correct and you always test the Debian updates before they become reachable via apt update; apt upgrade, right?
Thanks
Oh, I see Yuntian followed up here Rock5B Radxa Debian 12 image question: OK to install u-boot-rk2410 and remove u-boot-rknext? and said apt update; apt upgrade is NOT safe.
And refered here https://docs.radxa.com/en/template/sbc/os-config/rsetup#system-update .
Apparently rsetup has a Debian update function in it now, which is safe and is the designated way to update a Rock5B.
@radxaYuntian In which situations does it actually matter to use rsetup , i.e. what kind of situations does apt update; apt upgrade get into so it breaks the Debian installation and makes it unbootable? E.g. does it install broken kernels, or break u-boot etc.?