So i have this tool, where you can manipulate the registers of your SOC from your userpace. This is meant to be used by power users and most likely full of bugs but in past i leveraged this a lot when porting noname chinese tables to linux.
The idea is to mmap the SOC registers from user space and read and write to them. This tool additionally introduces a catalog approach where the target SOC’s memory registers are defined in a very simple format, and the tool calls for the registers for writing and reading.
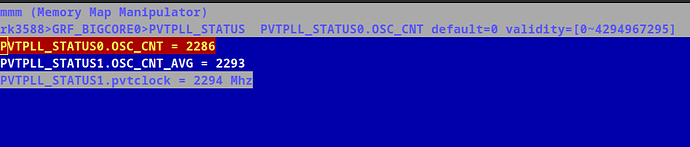
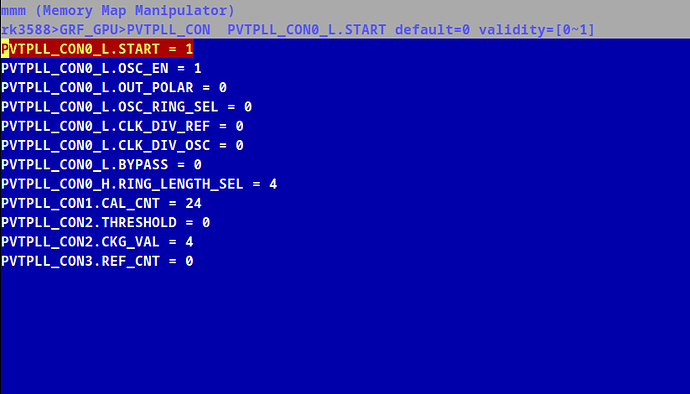
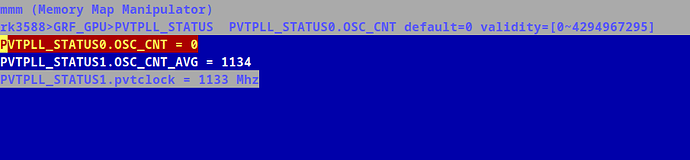
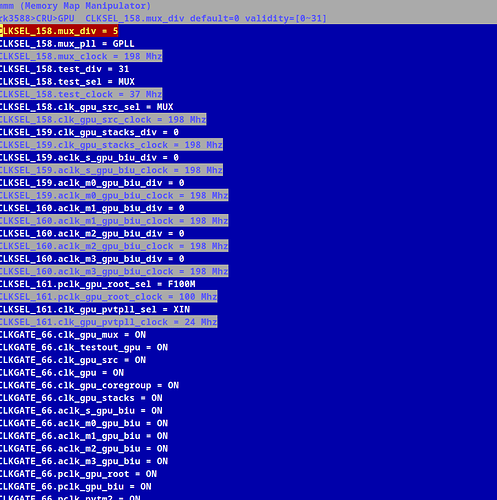
i have ported rk3588 GPIO Core to and you can clearly see al the GPIOs as below. But it can be extended, with whatever CORE is available in the SOC say, vop2, dramctl, vpu, gpu, and my actual target pvtm.
So yeah here it is in case someone picks an interest.
Here are the external signals on GPIO4 pins ie (A0=0, and A1=1)
[alarm@alarm mmm]$ sudo python mmm.py get -c rk3588 -d GPIO4 -r EXT_PORT
-c rk3588 -d GPIO4 -r EXT_PORT -p A0 = 0, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p A1 = 0, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p A2 = 1, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p A3 = 0, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p A4 = 0, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p A5 = 1, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p A6 = 0, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p A7 = 0, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p B0 = 1, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p B1 = 1, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p B2 = 1, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p B3 = 1, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p B4 = 0, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p B5 = 0, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p B6 = 1, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p B7 = 1, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p C0 = 1, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p C1 = 1, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p C2 = 0, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p C3 = 0, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p C4 = 0, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p C5 = 1, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p C6 = 1, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p C7 = 0, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p D0 = 1, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p D1 = 1, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p D2 = 1, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p D3 = 1, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p D4 = 1, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p D5 = 0, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p D6 = 0, (default=0)
-c rk3588 -d GPIO4 -r EXT_PORT -p D7 = 0, (default=0)
to start you can basically issue:
sudo python mmm.py get -c rk3588
WARNING: this tool can be very powerful, and as spiderman’s uncle said, it comes with big responsbilitiy. Ie: if you set a gpio to output true where it is phsically grounded without pull resistor, there is a certain risk that you might actually burn your socs GPIO output.
NOTE: to make it work you either need to pass iomem=relaxed to your kernel command line or you need to build your kernel with CONFIG_STRICT_DEVMEM=n CONFIG_IO_STRICT_DEVMEM=n options.
Edit: forgot to link the actual stuff